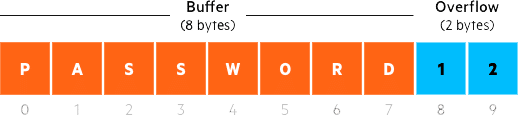
A Buffer Overflow takes place when a program overwrites other parts of a computer’s memory to store excess data, which can cause errors or even crashes. Hackers launch buffer overflow attacks by sending more data to a program than it expects (often including malicious code), leading the application to take over operating system memory. This action can allow unauthorized code to execute or simply lead to a system crash.
Buffer Overflow Example
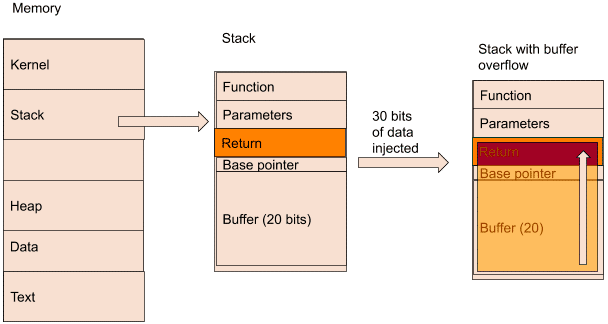
In the above image, memory is made of different parts. Between the stack and the heap, there is a buffer area, which allows both to grow during run time.
If we look at a stack in detail, we can see different sections:
Function: the calling function written by the developer
Parameters: the parameters needed by the function
Return: it tells the program what to do after it has executed the function
Base pointer: marks the start of a function stack frame
Buffer: the allocated space for data
In this example, we have a program that allocated 20 bits of buffer. If we inject more than that amount, say 30 bits, the data will overflow.
Because of the nature of the memory, the data will overflow upwards towards the function. Once it gets to the return section, that is where the problems start.
If an attacker injects data in the return that points to the address of malicious code, the program will run it, causing severe consequences.
What types of buffer overflow are there?
Here are the most well-known types of buffer overflow, beginning with the most common:
Stack overflow :This involves overflowing a buffer on the call stack, as described above.
Heap overflow :Same as stack overflow, but it takes place in an open memory pool.
Integer overflow :An arithmetic operation results in an integer that is too large for the integer type meant to store it.
Unicode overflow :Unicode characters are inserted into an input that expects ASCII characters.