- A SQL injection attack exploits vulnerabilities in a web server database that allow the attacker to gain access to the database and read, modify, or delete information.
- An example of a SQL injection attack is making the condition true by giving the identical value to a web page. These values can be inserted into a login as follows:
- Login: 1′ or ‘1’=’1 and Password= 1’or’1’=’1
- Login: 1′ or ‘1’=’1′;–
- When the Username argument is evaluated, ‘1’=’1’ will assess to TRUE, and an authentic username will be returned. You can do it practical on https://altoromutual.com:8080/login.jsp demo page to understand practically.
The Systametic Execution of SQL injection is explained in the image below
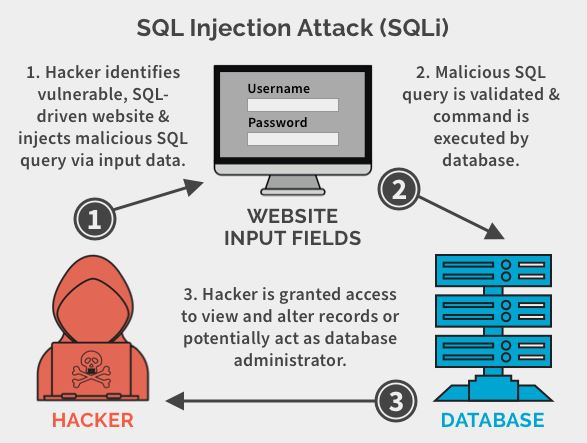
Input validation on the SQL Injection:
- There are measures that can be applied to mitigate SQL injection attacks.
- Web developer can check whether some suspicious characters are sent from the Login Page like ‘, “, ;, — , etc.
- In php projects use of MySQLi wrapper and object mapper can reduce chances.
- The best way to fix this sort of validation issue is to use php’s filter library. This library is designed to help you check and sanitize user input.
- Always store the Passwords in the Database server in the Encrypted Form.
- Use of these practices does not guarantee that SQL injection can be completely eliminated, but they will make it more difficult for Hackers to conduct these attacks.
Input Validation can help prevent :