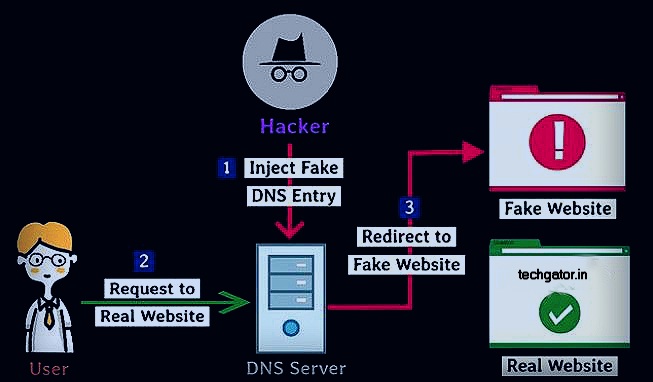
DNS poisoning is an attack in which the attacker can trick the DNS resolution server into resolving a domain with an incorrect IP address. DNS is used to map domain names like “techgator.in” to an IP address like “192.167.1.1”. Then the computer connects to the IP address and visits the website.
The Internet works on several DNS servers that temporarily store information with one another. Learning prevents DNS from repeatedly looking for the same web pages. These caches are kept for a period of time that is the life of the field in itself.
A DNS cache is poisoned if the server contains an invalid value or an incorrect IP address. If an attacker authenticates himself to a DNS server, he can change the value/IP address of several domains so that they point you to a fake IP address or fake website It also can be done by the man in the middle attack in which the hacker sniffs in the transmitted packets and sends the response, as shown in the figure.
This IP points to an official-looking website and can therefore be used for phishing attacks, or it can point to a website that installs malicious software on a user’s computer without the user’s knowledge.
The next time a user tries to visit an official website like “techgator.in”, the DNS gives them a spoofed IP address that redirects them to a spoofed website and makes them a victim.
DNS poisoning is extremely dangerous because it expands quickly. If multiple DNS servers get their information from a compromised DNS, they all have the rogue website and thus all become victims.